Use a KeyVault to create a certificate
I have always avoided using Certificates as I didn’t know how to create them, but it turns out that it is easier than I thought.
To test if this is possible we will create a linked service in ADF (azure data factory) and link to a Storage Account. We will use the Service Principal option to authenticate.
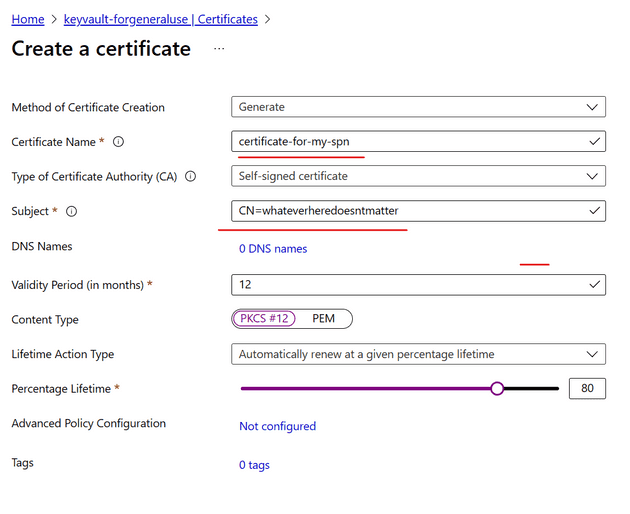
1. Start here by creating a certficiate in your KeyVault
Go to your KeyVault and under “Certificates” blade click on +Generate/Import
You can name your certificate what ever you want. And you can name the subject whatever you want to.
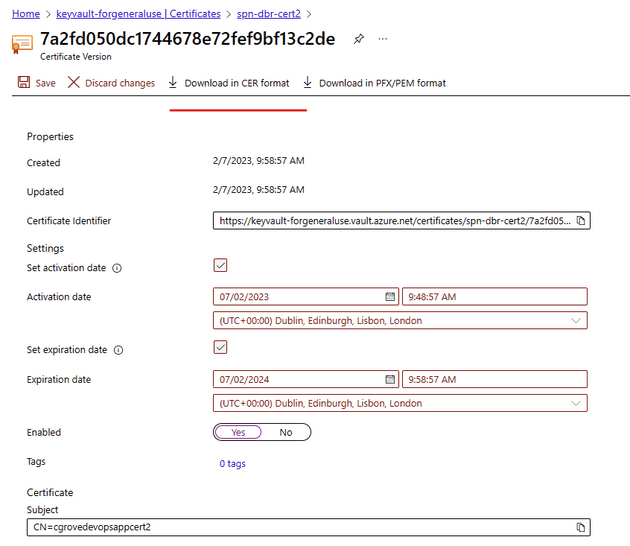
2. Download the CER format of the certificate to your local machine
Once the certificate is generated, then wait a second or two and then click on it. This window as you can see below will pop up.
Download the CER and save it to your laptop or desktop.
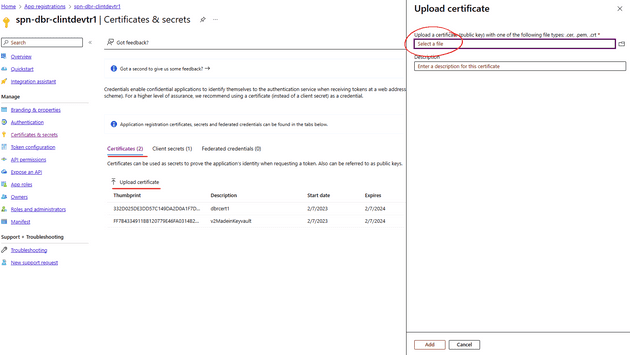
3. Upload to your App Reg
This part is simple, upload the CER file that you saved from step 2 which is on your local machine to the app registration.
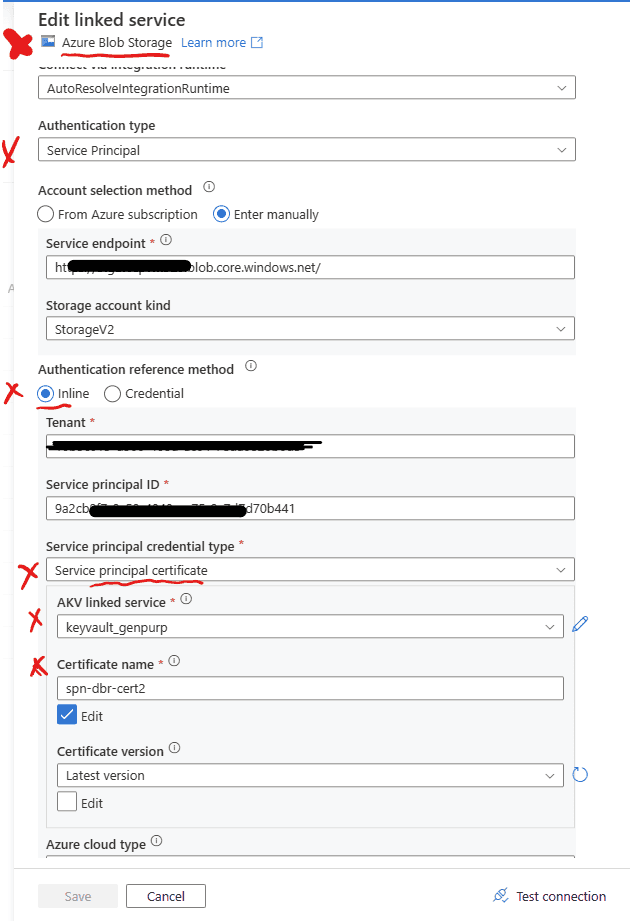
4. Set up a linked service in ADF to test if this works
- You would need to have a Storage Account. You would go to the IAM blade (which is RBAC) and then you would add your App Registration as a “Storage Blob Contributor
- Create a linked service in your ADF to the KeyVault. You need to give your ADF the ability to read the Certificates in your KeyVault. This can be done through Access Policies in your KeyVault
- Create a linked service from your ADF to your Storage Account and authenticate via Service Principal and using a Certificate. See image below
And now you can test your connection using that nifty button on the bottom right. You should be able to connect.
Happy coding!